1) Frameworks
As Soon As You Get The Target, You Must Identify The Technique Which Language Is Used To Build The Application.
Wappalyzer
Whois.Net
Source Code View
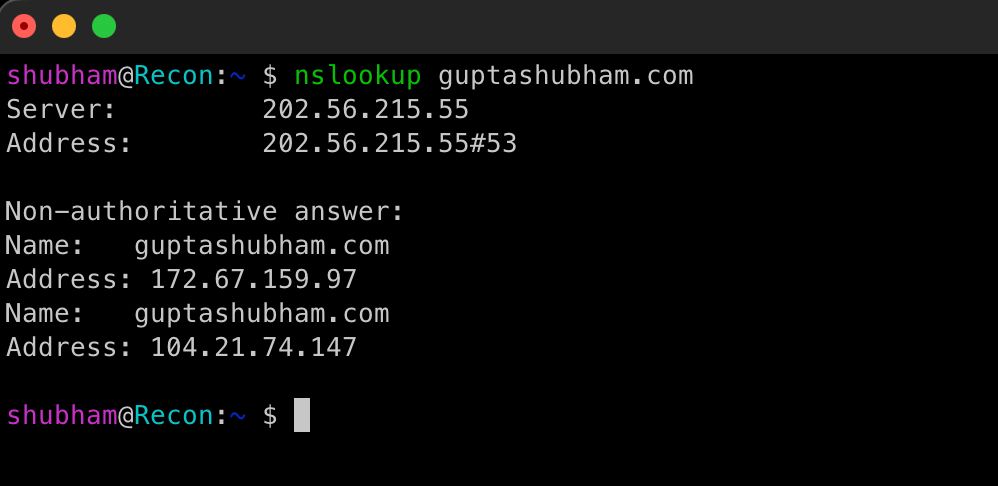
How I Identify The Client’s Domain’s Dns
I Use Nslookup To Verify The Domain Ip And Dns Entries.
Service Scan
To Check That On Which Port Which Service Is Running I Use Nmap
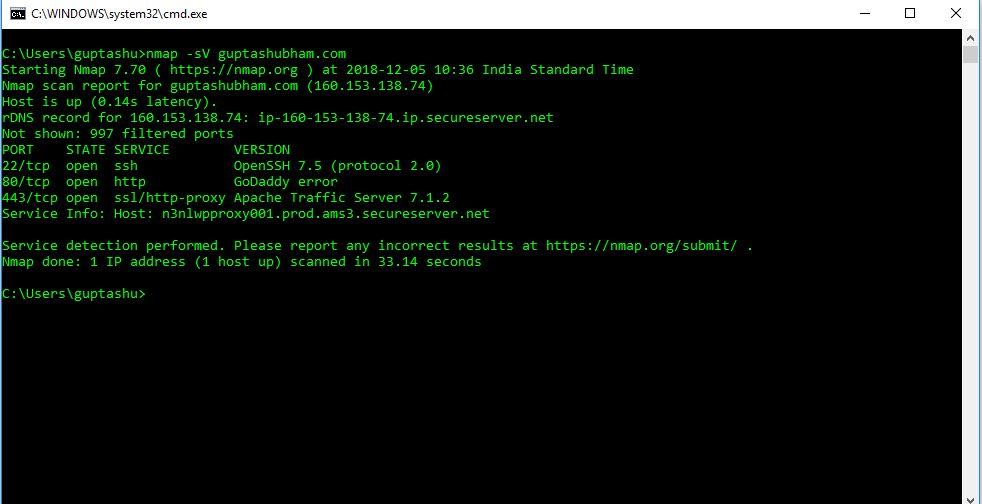
Nmap -Sv Abc.Com
If The Ping Scan Is Blocked Then Use
Nmap -Pn -Sv Abc.Com
After Finishing That, Understand How The Application Works.
I Visit Every Single Page As I Am A Noob User Of Particular Website And I Try To Understand That How The Web Application Works.
Find That Why This Web Application Is Made / Or You Can Say That Find That What Is The Purpose Of The Web Application.
- Manually Spider Whole Website And Understand The Purpose Of The Web Application.
- Easy Method To Spider A Website Is To Use Burp Suite.
- Configure Your Browser For Burp Suite.
- Turn Off The Interception And After Then Visit Every Single Page Of Your Target. (For Ex. Facebook = Social Networking, Paypal = Money Transfer)
After Knowing The Purpose Of The Web Application, Understand The Functionality That Functionalities Are Used To Fulfill The Purpose Of The Web Application.
- For Example (Which Technology They Are Using) Wordpress For Output
- Buddypress Some Websites Uses Api For Login And Registration Plugins
2) Behavior Analysis
When You Understand The Functionality, Start Surfing The Web Application. Intercept Every Page Requests.
- Remember Always Use Firefox
- Setup A Proxy With Burp
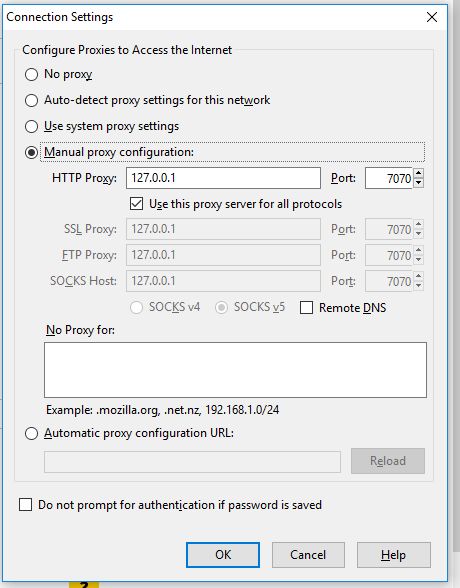
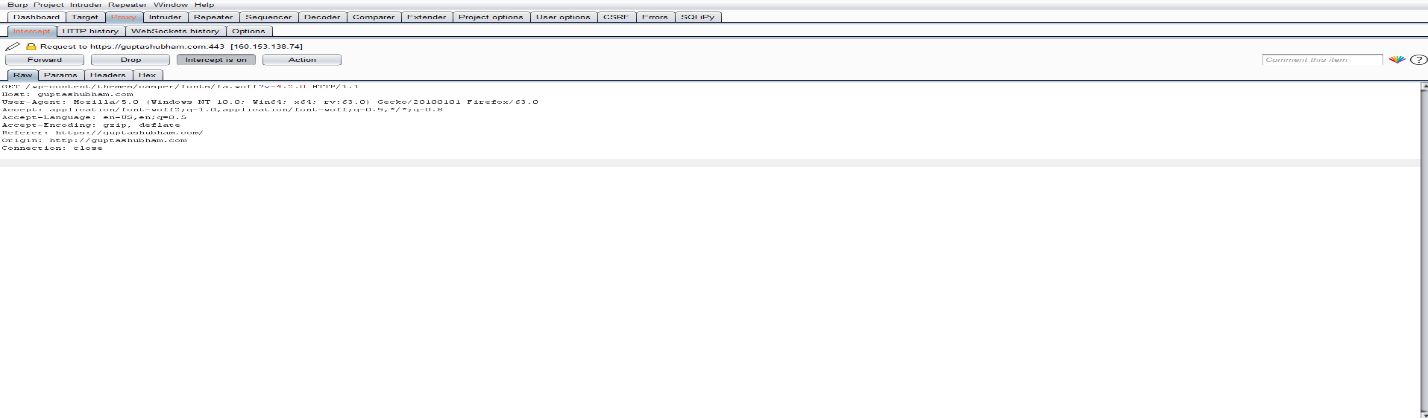
- Understand How The Request Goes
- Intercept The Request In The Burp
- Send The Request To Repeater
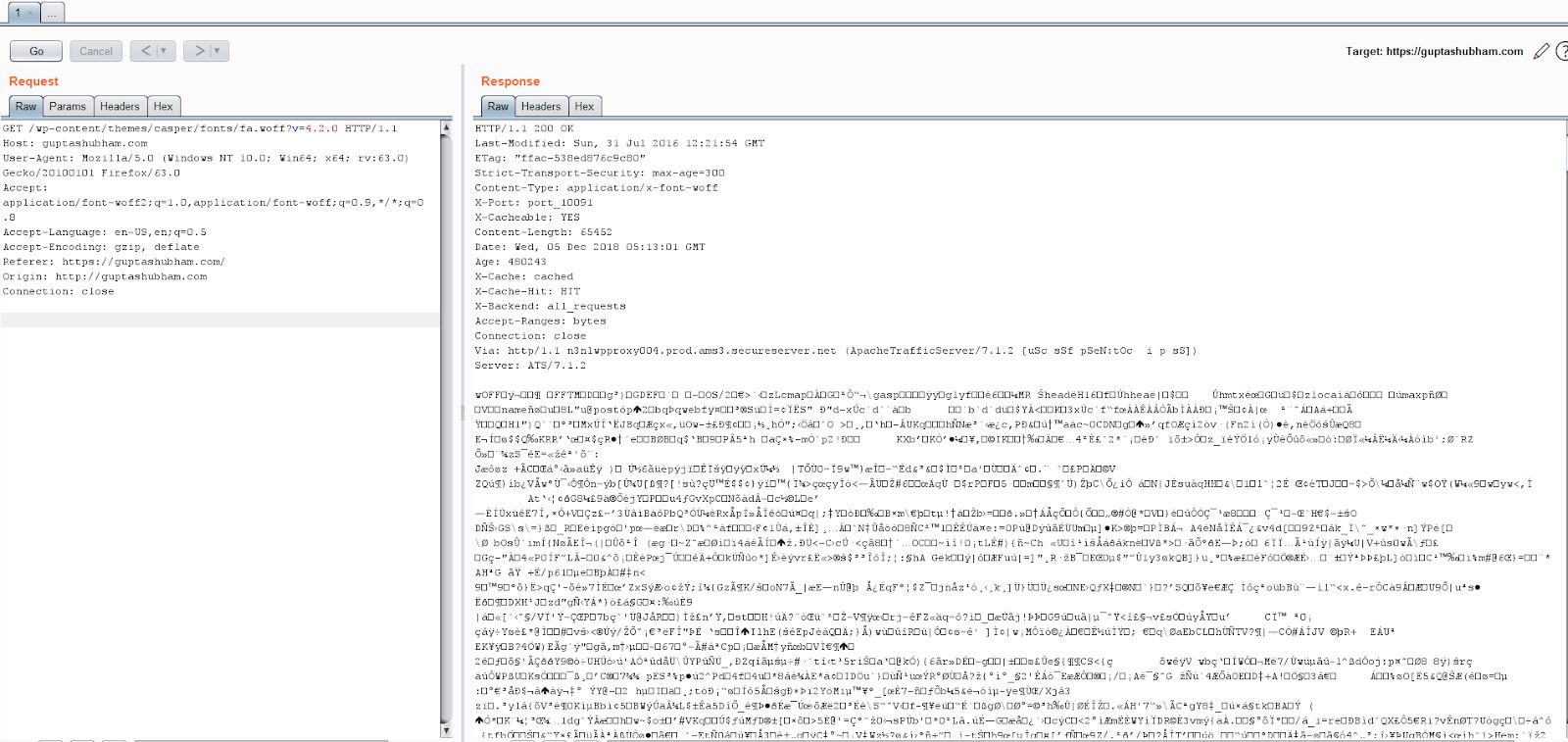
- Always Check Responses In Repeater
- More Tabs In Repeater = More Bugs U Will Find
- Check Every Page/Form’s Methods That Which Type Of Method Are They Using For Particular Page.
- By Intercepting The Request In A Burp, You Will Come To Know That Which Types Of Methods The Particular Pages Are Using.
- Check The Headers, That Which Headers Are Used For The Different Page’s Request & Response.
- I Typically Use Http Live Header
- But By Using The Burp You Can Find The Headers.
- Try To Find Out The Version Of The Framework.
- Wappalyzer Helps To Find The Version
- Sometimes It Shows The Version In Intercepted Request
- With The Help Of Source Code Review You Can Easily Find The Version Of Particular Javascript
- After getting the version of the Framework, check If any exploits available of that Framework.
- Shodan.Io
- Google Dorking
- Exploit-DB
- Darkweb
- I Personally Prefer Exploit-Db To Find Exploits.
3)Business Logic
- Understand The Web Application’s Business Logics For Every Functionality.
- If Site Is Using The Payment Gateway Then Understand The Payment Gateway.
- If There Is A Shopping Site Then How The Site Is Adding The Particular Product In A Cart.
- To Find All This Spidering Helps A Lot. (Google Dorks & Burp Spider).
- Find Out That Which Algorithms Are Used To Implement The Business Logic.
- Structure Of The Site. (Maltengo Tool)
- How The One Request Is Chained To Another Request
- How Is The One Page Is Chained To Another Page. (For This I Use Repeater In The Burp)
- If In A Single Page There Are Two Different Types Of Page, Then What Is Different Functionalities,
- Find Out The Encryption Of Every Algorithms, Values, Logics.
- Intercept Every Single Page’s Request. (For This I Use Burp Suite)
- The More Request You Intercept The More Parameters You Will Get.
- Deep Analysis.
- After Understanding The Web Application Start Hunting / Web Application Pen Testing By Following Owasp Standards.
4)Mapping The Application
- Explore Visible Content.
- When U Open Any Page Of The Web Application Explore Every Input, Hyperlinks, Input Boxes Which Are Visible.
-Tool ( Manual Web Application Surfing ). - Discover Hidden Content.
- Intercept The Request With The Help With Burp Suite And Discover Hidden Content And Parameters.
-Tools For This ( Burp Suite To Intercept The Request)
- Discover Default Content.
- There Are Some Contents In Every Site Which Are Default. So Have To Figure It Out That Are Thy Configured Properly Or Not.
For This You Have To Check And Test The Hidden Parameters As Well As The Visible Parameters. ( Intercept The Request In Burp Suite And Find The Hidden Parameters).
- Enumerate Identifier-Specified Functions.
- By Fuzzing The Request (Burp Suite Is The Best Way To Fuzz The Request) (Dir Buster, Fuzzing Parameters With Burp Suite)
- Fuzz The Parameters Which Are Sending The Requests.
- The More You Fuzz The More You Get.
- Test The Parameters.
- Enumeration On The Parameters.
- Fuzz The Parameters
- Brute Force The Parameters
- Manipulate The Parameters
5)Analys The Application
- Identify The Functionality
In The Web Application, There Are Many Functionality Has Defined. For Ex. In A Facebook You Can Make A Group. Now Making A Group Is A Functionality. So By Surfing The Web Application Identify All The Functionality.
- Identify The Data Entry Points
- Identify The Data Entry Points
- Identify The Data Entry Parameters
- Identify The Data Entry Methods
- Identify The Technology Is Used
- Source Code Review
- Map The Attack Surface.
- Manually By Surfing The Site.
6)Test Client-Side Controls
- Test The Transmission Of The Data Via Client.
- First Check The Http Method That Which Method The Website Is Using
- Enter Some Data Into Input Methods
- Intercept With Burp Suite
- Forward It And Check That How The Web Application Is Reacting.
- Test The Client Side Control Over The User.
- Enter Some Data Into Input Methods
- Intercept With Burp Suite
- Manipulate The Data /Request/Parameters
- Forward It And Check That How The Web Application Is Reacting.
- Test Thick-Client Components.
- Parameter Manipulation / Parameter Fuzzing / Hidden Parameter Fuzzing
7)Test Access Controls
- Test The Access Control Requirements
- Are You Able To Access Or Perform Any Task Without Specified Minimum Requirements?
- For Ex. Enter Minimum 6-Digit Password. However, I Am Able To Make An Account With a 4 Digit Password.
- Testing With Multiple Accounts
Make Multiple Accounts And Are You Able To Make Changes To Account 2 While You Are Logged In Into Account 1. If Yes, Find Out The Way.
- Testing With Limited Access
Try To Access The Things Which U Don’t Have Access. For Ex. You Are The Editor In A Particular Group, Try To Perform The Things Which The Admin Only Can Perform.
- Testing For Insecure Control Methods
Making Any Changes To Your Victim’s Account
8)Test For Logic Flaws
- Identify The Key Attack Surface
Make A To-Do List Of Particular Subdomains, Paths, Parameters Whom You Going To Test.
- Test The Multi-Stage Processes
- Make Different Steps That Which Standards Are You Going To Follow To Test The Web Application.
- Make A List Of It.
- Test Handling Of Incomplete Input
Test Every Single Input Methods.
- Test Trust Boundaries.
By Intercepting The Different Requests, You Can Find This.
- Test Transaction Logic/Methods.
- Test The Payment Gateway.
- Test The Html Code Manipulation.
- Test The Html Request Manipulation.
Owasp Top 10 Bugs
A1-Injections
Sql Injection (Manually)
- First I Try To Find Out Which Type Of Sql Injection Is This.
- If I Get The Admin Login Panel Then I Try 1’ Or ‘1’=’1-- - Or A’ Or’s’=’s-- - Which Are The Conditional Based Sql Injections.
- After Then I Try To Find That The Site Is Using The Get Based Method Or Post Based Method.
- If Site Is Using The Get Based Method Then Try To Find Out That Which Parameter Is Transferring The Data From The User To The Server,
- After Identifying The Parameter Which Is Transferring The Value, Try To Break Into The Query By Using ‘ (Quote) Or Maybe Sometimes Some Special Characters.
- Try To Find Out The List Of Columns
- Find Out Vulnerable Columns
- Find Out Table Names
- Find Out The Username & Password Table
- Try To Find The Vulnerable Part/Point From Where You Can Dump The Database.
- If The Site Is Using The Post Based Method To Transfer The Client Data To The Server Or Database, Then Set-Up The Proxy To Intercept The Request Into The Burp Suite.
- After Setting Up The Proxy, Intercept The Request Into The Burp And After Then Identify The Vulnerable Parameter Which Is Transferring The Data To The Database.
- After Then Try To Break The Query By Using ‘ (Quote).
- Try To Find Out The List Of Columns
- Find Out Vulnerable Columns
- Find Out Table Names
- Find Out The Username & Password Table
- Try To Find The Vulnerable Part/Point From Where You Can Dump The Database.
Blind Sql Injection
- After Finding That The Web Application Is Vulnerable To Sql Injection I Will Try To Figure It Out That Which Type Of Injection Is This.
- Now In A Blind Sql Injection Web Application Ask The Database The Conditions Which Are Going To Be True Or False.
- Now If They Show The Error Generic Messages Means It Is Vulnerable To Blind Sql Injection.
- Http://Newspaper.Com/Items.Php?Id=2 And 1=2
- By Using This Method, I Find The Blind Sql Injection.
- Time-Based Sql Injection
- Time-Based Sql Injection Basically Occurred When The Parameter Delays To Transfer The Client Data To The Database/Server.
- Http://Www.Site.Com/Vulnerable.Php?Id=1' Waitfor Delay '00:00:10'--
- As You Can See That I Have Delayed The Time To Transfer The Data And It Will Throw The Sql Error.
Ssi Injection
- Ssi Stands For Server Side Inclusion
- Ssi Is Used To Feed Html Content
- Ssi Perform Some Actions Before The Page Has Visualized.
- .Shtml Is An Extension Of Ssi Pages.
- Now Try To Put Or Insert “/></>(); Some Special Characters In Input Box Or In The Ssi Page & See The Output If They Are Filtering Or Not.
- Now If They Are Not Filtering Then Insert Some Html Tags Or Java Scripting Tags.
- If They Are Executing Then 90% Of Chances Of Ssi Injection.
- After Then Insert
<!--#Echo Var="Document_uri" -->
- Html Injection
- Html Injection Occurs When There Is No Proper Input Validation.
- This Can Lead To Defacement Sometimes.
- Frist Check That How The Site Is Reacting When I Insert The Special Characters. So, First I Will Insert “/></></><X>Test</S>.
- Of Check That How The Web Application Is Reacting. So, Go To View Page Source And Check It Out.
- If It Is Sending In Normal Form Then Insert Any Normal Html Tag For Example, <Marquee> Test </Marquee>
- Now Sometimes You Will Find That Your Payload Is Converting In Base 64 For It Is Converting Into The Url Endocing.
- Now In This Do Base 64 Encoding, Single Url Encoding Or Double Url Encoding.
- Sometimes Try To Understand How The Waf Is Reacting. By Using That Make Your Own Payload And Try To Exploit It.
Command Injection
- Command Injection Means Os Command Injection.
- It Means Somehow, I Can Execute The Command On Server’’s Os.
- There Are Two Types Of Os Command Execution.
- 1) Command Injection. 2) Blind Command Injection.
- Vulneble Url
- Http://Sensitive/Cgi-Bin/Userdata.Pl?Doc=
- Modified Url
- Http://Sensitive/Cgi-Bin/Userdata.Pl?Doc=/Bin/Ls|
- This Will Execute The Command “/Bin/Ls”.
- How To Find Command Injection In Post Based Method
Host Header Injection
- Intercept The Request Into The Burp Suite
- Send The Request To Repeater.
- Change The Host Name From To Any.
- Now Forward The Request & Check That Site Is Redirecting Or Not.
- If Its Redirecting Then The Site Is Vulnerable To Host Header Injection.
A2-Broken Authentication
- Understand The Mechanism
- In This You Only Need To Understand That How Authentication Mechanism Is Working.
- Try To Figure Out The Loop-Holes In The Authentication.
- Try To Find Out Low Or Poor Authentication Methods.
- Test Password Quality
- In This Try To Find That Which Type Of Password Mechanism Is Used.
- If Its Poor Then How Is It Poor.
- Find That Passwords Are Alpha-Numeric And Using Special Characters.
- Find Out The Min Length And The Max Length Of The Password.
- Test For Username Enumeration
- Username Enumeration Means Enumerate The Username Parameter To Find Out Existing User Or Users Usernames.
- For That Go To Forgot Password.
- Enter Any Email Or Username.
- Intercept It Into The Burp-Suite
- Now Send The Request To The Intruder.
- After Then Set Position On The Parameter Which Is Sending The Usernames To The Server.
- After Then Do A Brute-Force Attack Or Dictionary Attack On That Parameter And Check The Responses.
- Test Of Password Guessing Attack
- Open The Login Panel
- Intercept The Login Request Into The Burp Suite.
- Now Send The Intercepted Request To Intruder.
- After Then Find Out That Which Parameters Are Sending The Username And The Passwords To The Website.
- After Finding The Parameters Set The Position For That Attack And Start The Attack.
- Test Of Any Account Recovery Attack
- There Are Multiple Account Recovery Options Are Available To Recover Account.
- For Example, If You Forgot The Password Of Your Account.
- Go To Forgot Password & Entering The Email.
- Website Will Tell You To Check Your Email Address.
- When You Will Check Your Email Address Then You Will Find That The Website Has Sent A Recovery Code Which You Have To Enter Into A Page To Recover Your Account.
- Now You Will Open The Recovery Page, You Will Find Input Option Where You Have To Insert The Recovery Code To Recover Your Account.
- Now Many Times Recovery Parameter Is Vulnerable To Rate Limit Issue.
- Intercept The Recovery Page.
- Send It To Intruder.
- Set Position On Recovery Parameter.
- Start Brute Force Or Dictionary Attack.
- Test Any Remember Me Function
- When You Click On The Remember Me, The Username And Password Gets Stored In Browser Caches.
- Now Whenever You Will Open The Website, It Will Directly Login Into The Account.
- Sometimes What Happens If You Change The Password Then Still Remember Me Functionality Works.
- Sometimes Remember Me Functionality Has No Time Limitations.
- Test Any Impersonation Function
- For This You Need To Check That User’s Access Tokens Are Leaking Or Not.
- How Many Access The User Has Got After Getting The Access Token.
- Does The User Has More Access Then He Should?
- Test For Username Uniqueness
- Username Must Be Unique
- If The Usernames Are The Same Then Web Application Will Get Confused To Authenticate The Users.
- Exploits To Get Unauthorized Access.
- Try To Bypass The Authentications
- Check That If There Are Any 2fa Are Used Or Not
- If There Are Any 2fa Are Used Then Try To Bypass It.
A2-Session Management
- Understand The Mechanism
- Try To Understand That How The Sessions Are Managing.
- Test The Tokens
- First Login Into Web Application’s Account
- Then Use Edit This Cookie.
- Delete The Access Token.
- Now Try To Change Your Password.
- If It Is Working Then Web Application Has Poor Token Management.
- Test The Insecure Transmission Of Tokens.
- Now Sometimes Access Tokens Has Transmitted Over The Url Or By Using The Get Based Method
- Now This Is Totally Insecure Method To Transmit The Token.
- Sometimes What Happens They Uses Post Method But Still They Transfer Tokens Into The Normal Text Method Or They Use Poor Encryption Method To Encrypt The Token.
- Check The Disclosure Of Tokens In The Logs
- Now Sometimes Access Tokens Has Transmitted Over The Url Or By Using The Get Based Method
- Test The Session Termination
- In This Check That How Much Time Does The Website Takes To Terminate The Session.
- Test Session Fixation
- Login Into Your Account.
- Use Edit This Cookie, Export All The Cookies And Sessions.
- Now Logout From Your Account.
- Now Delete History And Stored Cookies.
- Now Again Load Website & Import The Cookies With The Help Of Edit This Cookie & Reload The Page.
- If You Get Logged In That Means Server Site Cookies Are Not Expiring And It Is Vulnerable To Session Fixation.
- Check The Cookie Scope
- In This Check That When Sessions And Access Tokens Gets Stored In The Cookies, How Much Access You Get.
- Are You Able To Perform Any Task Without Privileges?
A3-Cross Site Scripting
Stored Xss
- Find Out The Inputs Which Are Storing The Value In The Database.
- After Finding These Kind Of Inputs, Enter <Xss>Abc();//></Xss> Enter This.
- Go To View Source That Check That How Is It Working.
- After Then Enter The Xss Payloads.
- Try To Bypass Xss Wafs With Different Methodologies.
- If You Get The Stored Xss Then Try To Steal The Csrf Tokens Or Cookies.
Reflected Xss
- In This You Have To Find A Searchbox Or Any Parameter Which Is Reflecting The Value On The Page.
- After Finding These Kind Of Inputs, Enter <Xss>Abc();//></Xss> Enter This.
- Go To View Source That Check That How Is It Working.
- After Then Enter The Xss Payloads.
- Try To Bypass Xss Wafs With Different Methodologies.
- If You Get The Stored Xss Then Try To Steal The Csrf Tokens Or Cookies.
Dom Based Xss
- Dom Stands For Document Object Model
- For Me Dom Is Http://Abc.Com
- Now Lets Say Http://Abc.Com/A
- Http://Abc.Com/B
- This Are Paths
- If The Main Dom Which Is Http://Abc.Com Is Vulnerable To Xss Then The All The Paths Are Going To Vulnerable With Dom Based Xss.
- Self Xss
- Find The Input Parameters.
- Insert The Xss Payloads. If You Enter The Payload And As Soon As It Will Execute Then Might Be Possible That Site Is Has A Self Xss.
- When U Save The Payload And It Won’t Execute Then It Conforms That It Is A Self Xss.
- Flash Xss
- First Make A Xss.Swf File
<embed src="myflash.swf" quality="high" bgcolor="#ffffff" width="550" height="400" name="myflashmovie" flashvars="myvariable=Hello%20world&mysecondvariable=Goodbye" align="middle" allowscriptaccess="samedomain" allowfullscreen="false" type="application/x-shockwave-flash" pluginspage="http://www.adobe.com/go/getflash"/>
- Save This As A Xss.Swf
- Now Find The File Upload Option
- Then Upload Xss.Swf
- Suppose U Have Uploaded The On Http://Www.Abc.Com
- Then Open Http://Www.Abc.Com/Xss.Swf?Js=Prompt(1);
- Try To Convert Self Xss To Stored Xss
- Try To Chain Bugs (For Ex.)
- Csrf+Self Xss
- Clickjacking+Self Xss
- Post Based Self Xss
- Hidden Parameter Self Xss
A4-Insecure Direct Object Refrance
- Fails To Verify The User Authorization And Gives The User Access Which Is Restricted.
- Suppose There Is Some Account Which Only Has Authority To Update Blogs & This Account Can’t Change The Passwords.
- Now If The User Of That Account Who Has Only Access To Update The Blog Is Somehow Able To Change The Passwords Of Another Bogging User Then It Is Vulnerable To Idor.
- If The Reference Is Indirect Reference & It Fails To Limit Values To Those Authorized Users.
- You Have Only Authority To Update The Blogs From Your Account.
- You Update The Blog From Any Other’s Account Without Physical Access Somehow.
A5-Security Misconfiguration
- Software Application Is Out Of Date (It Includes Os, Web Application, Server, Database.)
- Suppose Web Application Is Using Wordpress 4.1 Which Is Vulnerable To Content Injection.
- Tiny Mce Editor
- Older Apache Servers Which Are Vulnerable To Rce
- Older Iis Servers Which Are Vulnerable To Authentication Bypass.
- Unnecessary Features Are Available Or Active. (Open Ports, Services, Pages, Accounts,)
- If There Is No Requirement Of Some Pages Like Blogs And Services,
- Ssh,Ftp Smtp Ports Open, Find Them By Using Nmap.
- Default Accounts
- Error Handling Function Discloses The Information
- Put Some Random Values Into The Url Or Into Input Methods, Sometimes The Web Application Throws The Errors Throws The 404 Or 403 Errors In Which It Also Discloses The Services, Versions And Other Details.
- Framework Security Settings
- Check The Version Of The Framework By Using Google Dorking.
- Find That Is There Any 0 Days Are Available
A6-Sensitive Data Exposure
- Any Data Is Stored In A Text Form
- Some Of The Information Such As Username, Passwords, Credit Cards Details Are Stored In Normal Clear Text Form In The Database.
- Data Transmission Is Done In A Clear Text Form
- Check If The Site Is Using Https Or Not.
- Intercept The Request Into The Burp & Check That Credentials Are In A Clear Text Or Not.
- You Can Also Test This By Using Wireshark Or By Doing Man In The Middle Attack.
- Old/Weak Cryptographic Methods Are Used.
- Check That Which Type Of Encryption Method Does The Web Site Is Using,
- If Its Poor Or Outdated Version Then It Can Lead To The Data Breach
- Missing Headers
- Use Http Live Header
- Open The Web Application And Just Reload The Page
- You Will Find All The Headers Which Are Used On Particular Page.
- By That You Can Find That Which Headers Are Missing.
A7-Missing Function Level Access Control
- Ui Shows Unauthorized Functions
- Sometimes Improper Ui Discloses Many Information.
- Some Of Hyperlinks Redirects To Admin Pages Or Hidden Pages.
- Server Side Authentication Is Missing / Authorization
- Sometimes The Authentication Is Missing Suppose There Is An Admin Login Page Like
Abc.Com/Admin/Login.Html
- When I Will Simply Change The Path Name From Login.Html To Index.Html Then I Will Get The Access Of Admin
- Ex. Abc.Com/Admin/Index.Html
- Same Thing I Check The Authority Of Every Single User.
A8-Cross Site Request Forgery
- Csrf Token Is Not Implemented
- Intercept Every Single Page Which Has Some User Details & Check The Csrf Token Is There Or Not. If It’s Not Then Its Vulnerable To Csrf.
- Focus On State Changing Functions.
- When User Is Requesting To Server Then Intercept The Request And Check That What And Which States Are Changing By That Action And Which Functions Are Used.
- Token Manipulation Bypass.
- Intercept The Request, If There Is Csrf Token, Remove It And Forward The Request.
- Try To Change Some Values Of Csrf Token.
- Try To Capture Csrf Token With Xss.
A9-Using Components With Known Vulnerabilities
- Does The Site Is Currently Using Any Vulnerable Component, Frameworks, Library Or Not.
- Find The Component Version, Framework Version, Library Version.
- Check That If There Are Any 0 Days Or Exploits Are Available In Market.
A10-Unvalidated Redirects & Forwards
- Review The Code For User Which Redirects, Response Code, Redirection Parameter.
- Whenever I Find Something Like This
Http://Example.Com/Example.Php?Url=
- I Intercept The Request And Start Playing With Url Redirection Parameter.
Http://Example.Com/Example.Php?Url=Http://Malicious.Example.Com
- Sometimes I Put @Example.Com
- Sometimes %2fexample.Com
../../@Example.Com
..\@Example.Com
Captcha
- Send Old Captcha Value.
- Send Old Captcha Value With Old Session Id.
- Request Captcha Absolute Path Like Www.Url.Com/Captcha/1.Png
- Remove Captcha With Any Adblocker And Request Again
- Bypass With Ocr Tool (Easy One)
- Change From Post To Get
- Remove Captcha Parameter
- Convert Json Request To Normal
- Try Header Injections
Test For Input Based Vulnerability
- Fuzz All Request Parameters (If Got User, Add Headers To Fuzzer)
- Identify All Reflected Data
- [Reflected Xss]
- Http [ Header Injection] In Get & Post (X Forwarded Host)
- Rce Via Referer Header
- Sql Injection Via User-Agent Header
- Arbitrary Redirection
- Stored Attacks
- Os Command Injection
- Path [Traversal], Lfi And Rfi
- Script Injection
- File Inclusion
- Smtp Injection
- Native Software Flaws (Buffer Overflow, Integer Bugs, Format Strings)
- Soap Injection
- Ldap Injection
- Ssi Injection
- Xpath Injection
- [Xxe] In Any Request, Change Content-Type To Text/Xml
- Stored [Xss]
- [Sql ]Injection With ' And '--+-
- [Nosql ]Injection
- Http Request [Smuggling]
- [Open Redirect]
- Code Injection \(≪H1≫Six2dez≪/H1≫ On Stored Param\)
- [Ssrf ]In Previously Discovered Open Ports
- Xmlrpc.Php Dos And User Enumeration
- Http Dangerous Methods Options Put Delete
- Try To Discover Hidden Parameters
Other Checks
- Segregation In Shared Infrastructures
- Segregation Between Asp-Hosted Applications
- Web Server Vulnerabilities
- Dangerous Http Methods
- Proxy Functionality
- Virtual Hosting Misconfiguration (Vhostscan)
- Check For Internal Numeric Ip's In Request
- Check For External Numeric Ip's And Resolve It
- Test Cloud Storage
- Check The Existence Of Alternative Channels (Www.Web.Com Vs M.Web.Com)